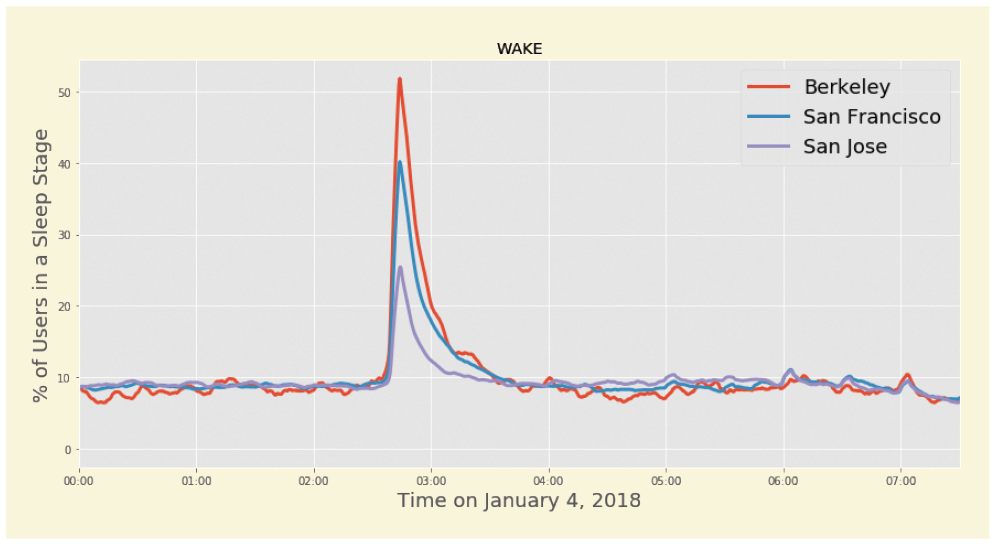
On Jan. 4, a magnitude 4.4 earthquake hit northern California at 2:39 a.m. Instantly, Fitbit data spiked, as anyone wearing the wristband fitness and sleep tracker was jolted awake.
The spike was largest in Berkeley, the epicenter, and the quake’s impact on San Francisco and San Jose could be mapped according to the sleep data Fitbit collects. (See graph).
Who needs U.S. Geological Survey monitoring stations?
“Fitbit knew there was an earthquake before the U.S. Geological Survey, because in the wee hours of the morning everybody in this region simultaneously woke up,” says University of Florida researcher David Arnold. “And you could tell the severity by location using Fitbit data.
“A year ago nobody would have thought of this,” Arnold says. “But it’s a distributed sensor network in a real-world condition; a fast and powerful demonstration of a new way to use anonymized fitness tracker data.”
Welcome to the internet of things, where the tiny sensor is about to flex its muscle.
Wireless World
Today, the novelty of the internet of things enchants us. It’s cool to check our refrigerator for milk as we stroll the grocery aisles or convenient to take a cellphone picture of a check, the funds magically appearing in our bank account.
But these are small feats, already old news. The growing connection of the physical world to the cyber world is tantamount to an Industrial Revolution, and it’s about to change everything, says John Harris, chair of UF’s Department of Electrical and Computer Engineering. Literally everything.
“It’s a scary time,” Harris says. “There is a world of potential, and we will need multidisciplinary teams with help from experts in psychology and law to make real progress.”

Harris says UF is emerging as a leader in assembling teams of researchers to explore the science of the internet of things. The cyber-physical intersection is job one for the newly created Warren B. Nelms Institute for the Connected World and keeping it secure is the mission of the Florida Institute for Cybersecurity Research. In March, a brand-new center, the National Science Foundation Center for Big Learning, with UF as the lead institution, was funded. And, at only three years old, the MIST — the Multi-functional Integrated System Technology — Center is a veteran in technologies that enable the IoT.
Sandip Ray, who came to UF from the semiconductor industry, says UF’s strong suit is an ability to collaborate among disciplines in a research environment that is speeding up and needs to move even faster. Traditionally, he says, hardware is developed and then software follows. Today, hardware and software are co-evolving, and that complicates everything.
“If you need to build the hardware and the software together, how do you do that?” asks Ray, one of four Endowed IoT Term Professors. “How do you validate a software that is supposed to run on a hardware that has not yet been built?”
The advantage of academic research as opposed to industry, he says, is the variety of disciplines that can contribute to a solution.
“There are traditional pillars in electrical engineering and computer science, and we can take the research from all of them to work together to meet the needs of the connected world,” Ray says.
Defying Definition
Sensors won’t rule this brave new world alone. They will need connectivity — to each other and the internet — and they will need computing power. It takes all three attributes to make our devices “smart.” Already there are more smart devices in the world than people, and the National Science Foundation forecasts 50 billion smart devices will exist by 2020. Before long, NSF predicts, there will be 1 trillion sensors at large in the internet of things.
Defining the internet of things is tricky. Ask a UF researcher for a definition and you get a grimace or a shake of the head. No one will do it.
Yier Jin, the first hire for the Nelms Institute, says it is too big to define.
“To define it accurately, it literally means everything, and then the definition loses its meaning,” says Jin, an Endowed IoT Term Professor. “That’s why we do the work without arguing about what it is.”
Arnold says it’s like defining an elephant by touch: the definition depends on which part of the elephant you are touching.

“If you go back to 1985 and tell people, ‘There’s this thing coming; it’s called the internet; it’s going to be exciting,’ it would be hard to explain the significance,” Arnold says. “Now you say ‘internet’ and everybody knows what it is. Interestingly, what everybody thought the internet would do in 1985 was allow computers at UF to talk to computers at NASA. It’s so much bigger than that. What is the internet? Now I can sit in my car at a traffic light and do a banking transaction.
“So anyone who looks you in the eye and says this is what IoT is, I wouldn’t believe them. They don’t know; nobody really knows. It’s a very squishy, smushy definition, and that’s the problem.”
What is known is that IoT brings together technologies that mostly were unavailable a decade ago. Sensors have gotten smaller and more powerful, wireless transmission capabilities are commonplace, and the computing power needed to collect data and analyze it is new.
“Before, even if I had sensors that could measure everything on campus, the computing power to make sense of it didn’t exist. What would I even do with all that data? How would I make sense of millions and millions of data points?
“What we are seeing is this convergence of engineering and science, all these pieces coming together at this point in time,” Arnold says.
Secure Connections
Mark Tehranipoor, the co-director of the Florida Institute for Cybersecurity Research, recalls a story about a consultant who was asked to evaluate the security of voting machines in Virginia. The consultant broke into the system in 10 seconds. The password was “abcdef.”
There’s no substitute for vigilance — or a good password — in cyberspace.
Tehranipoor says educating users would eliminate some problems. Other problems will require more of the kind of work done at the institute.

“Attacks are getting more and more sophisticated every minute,” says Tehranipoor. “Roughly every minute, there are about 1,000 new malwares generated.”
If you think you have issues with suspicious emails, consider UF. Tehranipoor says UF received 70 million to 80 million emails last year. Of those, about 64 million were phishing emails, and most of those attacks were from bots, surfing the internet, waiting for someone to click on an email that seems innocent but isn’t.
Once a bot penetrates your computer with a worm or a virus, it is in control. It can lurk for a while, monitoring your activity, spying on your bank accounts and passwords, then encrypting your files. One common attack is ransomware, an area Tehranipoor predicts will grow, in which your device or your data is held hostage until you pay up.
That’s what happened to the city of Atlanta in March, when ransomware locked up all of the city’s major computing systems.
On a more personal level, a bot that detects that you are on vacation could open your garage door and turn off your alarm system, then blackmail you until you pay up.
Bots can also lock you out of your laptop, restoring access for a fee. This could be an easier fix, Tehranipoor says, if you are following good cyber hygiene, backing up your system daily. Then the threat is empty. You simply reformat your computer and use your backup to retrieve your data.
If you are prone to clicking “try later” when your operating system reminds you to update, Tehranipoor says, break that habit now.
“You should accept the update,” Tehranipoor says. “You don’t know exactly what they’re updating, but I assure you, more often than not, they are trying to patch vulnerabilities.”
Part of the issue with security of IoT devices is providing the power to perform security functions on top of the computational functions for which a device is designed. Providing that level of security requires about 20 to 30 percent more power, and more power means the device will be more expensive, or less convenient, especially for battery-powered smart mobile devices. For example, adding security to a pacemaker would make the battery discharge more quickly. Would a patient choose security if it meant undergoing surgery in two years to replace the battery, or convenience, and delaying surgery for four years?
“Most IoT devices have enough power to connect and send data, but not enough power to run complex security algorithms,” Tehranipoor says.
If you have 20 devices connected to the internet, it only takes one with weak security for all of them to be compromised. Still, staying off the internet is not an option. The internet of things will not be avoidable, says Tehranipoor.
“There is great potential for great disruption,” Tehranipoor says. “Anything connected to the internet inherently becomes insecure.”

While Tehranipoor and other researchers work on the security of hardware, software and networks, he says three pieces of advice could help almost any user of a smart device: don’t click on an email if you don’t recognize the sender; create a strong password; and avoid connecting to unsecured Wi-Fi.
Ray says it makes sense that in the burgeoning world of connected devices, even a small percentage of bad actors can cause significant harm.
“If there are billions of devices connected to the internet, then there are probably millions of devices that are malicious,” says Ray. “So every device has to work in this environment.”
Black Hats, White Hats
Ray and Jin are a team of sorts when it comes to hacking smart devices, an offense vs. defense approach.
“I am the blue team to Yier’s red team,” Ray says. “His job is to find the vulnerabilities, and my job is to make a system secure so he cannot attack me.”
That’s a tall order, considering that Jin is known for his ability to crack the security systems of common IoT devices, including the Nest thermostat.
Much has changed since Jin and a team of students hacked a Nest thermostat in 2014. One of his students said his grandmother had just received one as a gift. The team bought one and went to work, testing the device to see what would happen. They noticed some vulnerabilities and suggested a fix to the company, which snubbed them.
“I thought, ‘Maybe we should put on our black hat, and see what the issue is,’” Jin says.
The hack — officially called penetration testing — was successful, and the team published their research in a journal. The reaction from Nest was immediate.
Today, companies are more receptive to learning about vulnerabilities in their devices, says Jin, who has catalogued the security flaws in a variety of commercial IoT devices in addition to the Nest.
“We feel it’s our duty, and we are happy that people eventually do take security seriously,” says Jin, who has a Nest thermostat in his own home.
Ray worked at NXP Semiconductors on technology for the vehicles of the future and says one challenge is that traditional approaches to security don’t work for technologies that enable self-driving vehicles. For example, if you are surfing the internet and your computer detects a suspicious website, it prevents you from accessing it.
“But think about a car going 70 mph that gets a communication about something suspicious,” Ray says. “You cannot just stop the car. When you have real-time requirements, you must address the situation much more gracefully.”
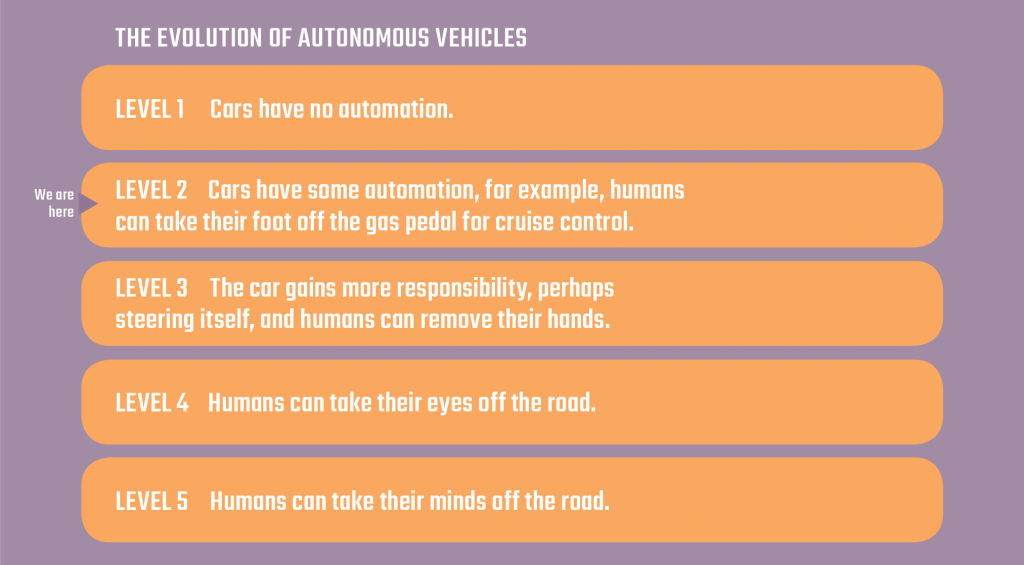
The road to fully autonomous cars is complicated. Today is level 2, he says, with some automation, for example, taking our foot off the gas pedal for cruise control. The driver, however, is responsible, and must be alert. At level 3, the car gains more responsibility, perhaps steering itself, and humans can remove their hands. At level 4, humans can take their eyes off the road, and at level 5, take their minds off the road.
Another challenge is that we don’t change cars the way we change smartphones.
“It’s not like we can take all the current vehicles off the road and replace them with autonomous vehicles,” Ray says. “So there will be a combination of the cyber world and physical world. When an automatic car is driving, you cannot assume the other cars have the same level of automation.”
Still, for the sake of road safety, automated driving is a worthy goal, Ray says. About 94 percent of accidents today are because of human error. Other philosophical issues also will need to be addressed, Ray says, such as how a car should perform in certain situations.
“Suppose the car has one passenger, a driver, and suddenly it senses a whole bunch of children crossing the road. Does it veer off the road and kill the driver or does it drive into the children?” Ray says. “What is the car supposed to do?

“Humans don’t have to decide because humans don’t react quickly enough,” Ray says.
Harris, who has just taught his teenagers how to drive, says he believes they will not need to teach their own children to drive.
Ray sees rich research opportunities.
“This is an area we know is critical, we know we don’t have the science for it, and we know we need it very, very quickly,” Ray says. “There is nothing more exciting. As a scientist, we thrive on uncertainty. Is it scary? Yes, it is very, very scary, but it’s good to do something that scares you. As a researcher, that’s a good maxim.”
Billions to Trillions
The NSF prediction that we are mere years away from unleashing a trillion sensors on the world has spawned an annual meeting called the Trillion Sensor Summit, at which UF’s Toshi Nishida has presented. The question is more than theoretical.
As data proliferates, zipping into cyberspace for interpretation, then back to the physical world in the form of information we can use, the humble sensor will take center stage. Already we can implant and swallow sensors, sensors on our infrastructure can tell us the condition of roads and bridges, and newer home appliances can sense our environment.
We may need a trillion sensors to make sense of this new world, scientists say. By one measure, humans create as much information every two days as they created from the time of cave paintings to 2003.
“When we talk about sensor networks with trillions of data connection points, those are giant numbers,” says Arnold. “How would we even manufacture a trillion devices? How do we crunch the data?
“To unleash the full potential of the IoT, it’s not like one professor or one team of professors could do this,” Arnold says. “The real power is putting out extraordinary numbers of sensors in real-world situations and then seeing what happens.”
Sources:
- David Arnold, George Kirkland Engineering Leadership Professor
- John Harris, Chair and Professor of the Department of Electrical and Computer Engineering
- Mark Tehranipoor, Co-director of the Florida Institute for Cybersecurity Research
- Sandip Ray, Endowed IoT Term Professor
- Yier Jin, Endowed IoT Term Professor
This article was originally featured in the Summer 2018 issue of Explore Magazine.

